Silverleaf Computers & Accessories Ltd. Malawi
We Are a Managed Service Provider













Cloud Computing

Backup & Disaster Recovery

Cyber Security
Compliance & Learning

Communications
Managed Service Provider, Cyber Security
Network Security, Disaster Recovery As A Service

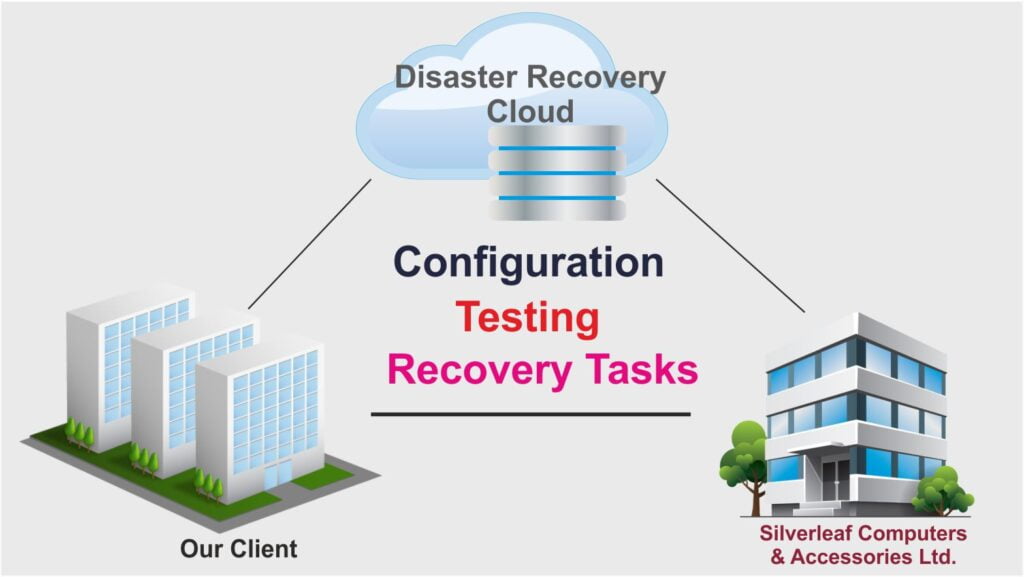
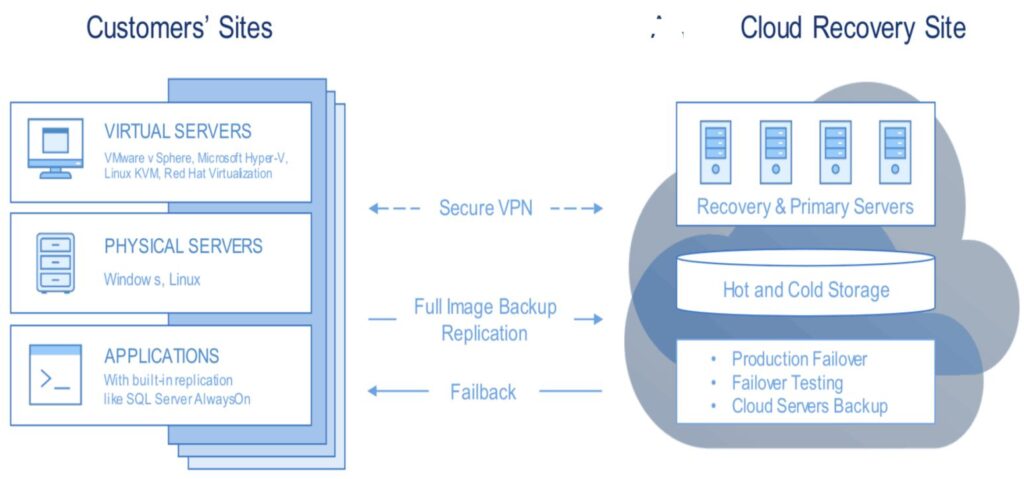
Learn More about Disaster Recovery As A Solution

Acronis Cyber Cloud
Protect all clients, whatever their hardware, software, or use case

Bluedog
bluedog offer businesses of all sizes the type of advanced network protection that previously only large corporates could afford.

Heimdal Security
Heimdal Security have been leading the fight against cybercrime, developing new technologies and providing intelligence to protect over 1 million users against cybercriminal attacks and data security breaches.

CyberSmart
CyberSmart is the easiest way to achieve British government standard security certifications. CyberSmart is an automated platform that allows clients to achieve certification and maintain their compliance, easily and automatically. CyberSmart special

Hornetsecurity
The product portfolio covers all important areas of email security, including spam and virus filters, legally compliant archiving and encryption, as well as defense against CEO fraud and ransomware.

ISL Online
focuses on ease of use and is extremely feature rich allowing you to offer efficient and dependable remote support to end users. The solution allows you to control an unlimited number of unattended remote computers

KEEPER
Cybersecurity starts with password security. Keeper is the leading cybersecurity platform for preventing password-related data breaches and cyberthreats.

KnowBe4 Security Awareness Training
KnowBe4 is the world’s largest integrated platform for security awareness training combined with simulated phishing attacks.

Mi Crow Courses
Mi Crow believe less is more when it comes to staff training. Mi Crow’s 3 minute videos get right to the point letting employees learn what they want, when they want.

PrivIQ
PrivIQ (formerly GDPR365) is a GDPR compliance management service with powerful workflows and collaboration tools.

Redstor
Redstor is a leading cloud data management provider delivering automated cloud backup and disaster recovery.

Safe-t
Lock down your access. Secure your resources. The “Zero-Trust” model has been widely accepted, for a long time, as an organisation’s goal for secure access. However, in practice, without “starting again” and migrating all existing infrastructure to a new SDP (Software Defined Perimeter) access network, implementing Zero-Trust concepts proves complex, very expensive and extremely time consuming.

ThreatAware
Centrally monitor and manage an extensive range of security and productivity applications. The ThreatAware platform is an agentless, multi-tenanted, vendor-agnostic solution that provides a single pane-of-glass